Cloud Security
Our Cloud Security Testing services help you proactively identify and remediate vulnerabilities in your cloud infrastructure, ensuring robust protection against cyber threats and compliance with industry standards.
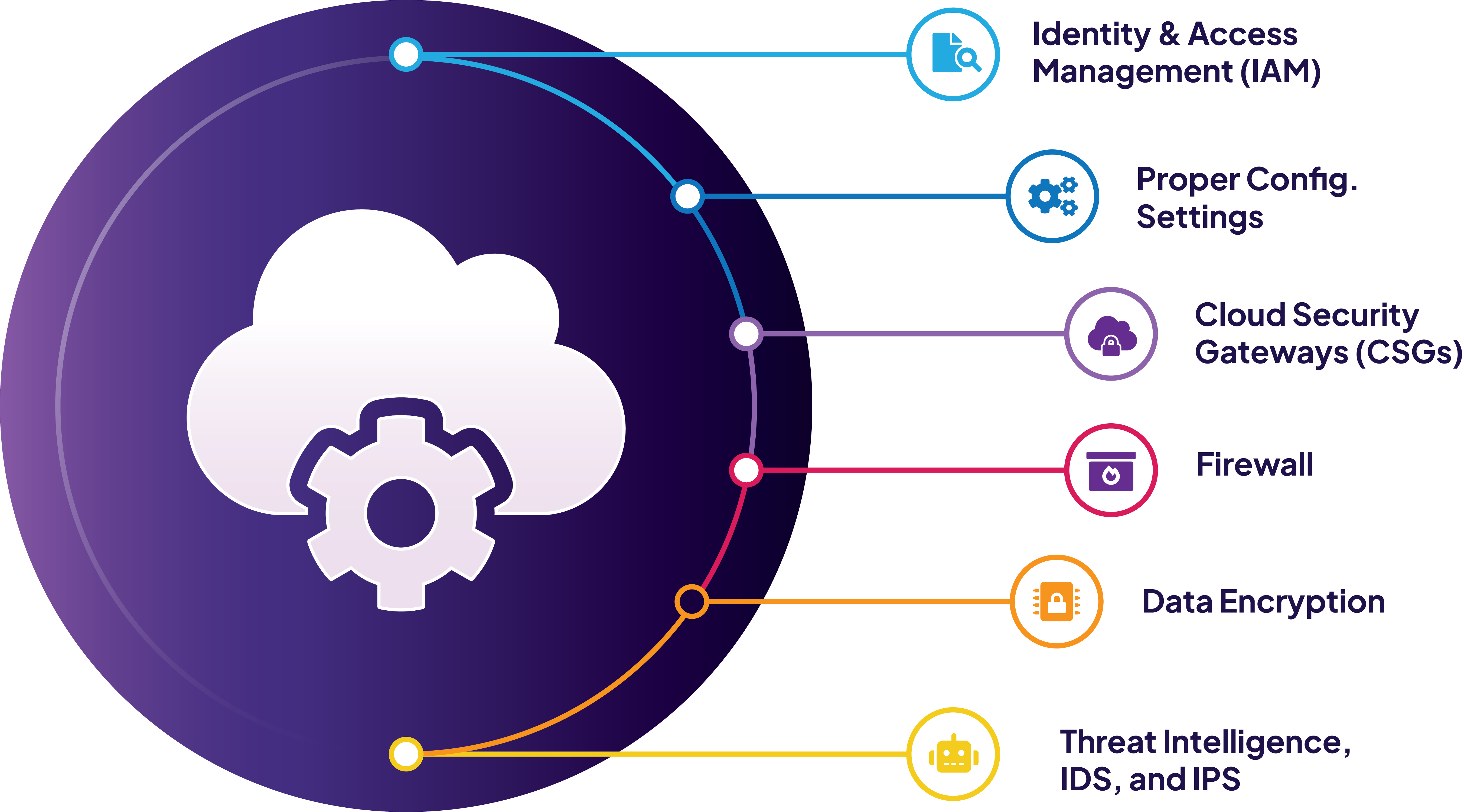
The Importance of Cloud Security
As organizations increasingly move their operations to the cloud, the potential for cyber threats grows. Cloud environments introduce unique security challenges that require specialized expertise to manage. Ensuring the security of your cloud infrastructure is essential to protect sensitive data, maintain business continuity, and meet regulatory requirements.
Our Approach
At Pretera, we systematically identify vulnerabilities within cloud environments through a comprehensive approach. We begin by assessing the cloud architecture and service models (IaaS, PaaS, SaaS) to tailor our testing methodology. We then conduct reconnaissance to gather information about the cloud infrastructure, identifying exposed services and potential attack vectors. Following this, we perform targeted penetration testing to simulate real-world attacks and evaluate security measures. Finally, we provide detailed analysis and actionable recommendations for remediation, ensuring clients understand the findings and can enhance their security posture effectively.
Key Features of Our Cloud Security Testing Services
- Office 365 Security Testing: Ensuring the security of your Office 365 environment against potential threats.
- Configuration Review: Assessing the security configurations of your Office 365 setup to ensure compliance with best practices.
- Access Controls: Verifying that access controls and permissions are properly configured to prevent unauthorized access.
- Data Protection: Ensuring that data stored in Office 365 is encrypted and protected against breaches.
- AWS Security Testing: Evaluating the security of your Amazon Web Services (AWS) infrastructure.
- Identity and Access Management (IAM): Reviewing IAM policies and configurations to ensure secure access control.
- Network Security: Assessing the security of your VPC, security groups, and network ACLs to prevent unauthorized access.
- Data Security: Ensuring that data stored in S3 buckets, RDS, and other AWS services is secure.
- Google Cloud Security Testing: Securing your Google Cloud Platform (GCP) environment against threats.
- Configuration Management: Assessing the security configurations of your GCP resources to ensure compliance with best practices.
- Access Management: Reviewing IAM roles and policies to ensure secure access control.
- Data Protection: Ensuring that data stored in Google Cloud Storage, BigQuery, and other GCP services is encrypted and protected.
- Azure Security Testing: Evaluating the security of your Microsoft Azure infrastructure.
- Identity Management: Reviewing Azure Active Directory configurations and access controls.
- Network Security: Assessing the security of virtual networks, NSGs, and other network components.
- Data Security: Ensuring that data stored in Azure Blob Storage, SQL Database, and other Azure services is secure.
- Compliance and Best Practices: Ensuring that your cloud environment meets industry standards and regulatory requirements.
- Regulatory Compliance: Assessing your cloud infrastructure for compliance with regulations such as GDPR, HIPAA, and PCI DSS.
- Security Best Practices: Implementing cloud security best practices to enhance your overall security posture.
Detailed Reporting and Remediation Guidance
Our detailed penetration testing report is written in understandable terms and provides clear and actionable information about identified vulnerabilities, their potential impact, and recommended remediation steps. This allows your team to quickly understand and start addressing issues immediately.
- Executive Summary: High-level overview of the findings aimed for management and delivered shortly after the assessment.
- Technical Details: In-depth reporting with details at every step of our penetration testing services, helping your technical teams replicate the vectors easily and remediate swiftly.
- Report Readout: We provide report read out for your management, accelerating the understanding of the report and clarifying any unclarities on the spot.
- Remediation Guidance: Post-pentest step-by-step support and guidance on how to fix identified vulnerabilities and accelerate the remediation
- Free Retesting: Following the remediation of identified vulnerabilities, we offer a free retesting of all the vulnerabilities to ensure everything has been remediated.
Why Work With Us
Our team of experienced security professionals brings deep knowledge and experience of application security and the latest threat landscapes. We operate as your internal team, seeking to always understand the challenges you face and ensure you solve them, always. Work with us and experience open and transparent communication throughout the testing process providing real-time updates and insights. This collaborative approach ensures that you are always informed and can prioritize remediation efforts.
KeyPoints
-
Simulated Reconnaissance
-
Attack Surface Mapping
-
Attack Replication
-
Dynamic Application Coverage
-
Flexible Delivery Models
-
Diverse Language Coverage
Cloud Security Services
Office 365
Our Office 365 Security services help you proactively identify and remediate vulnerabilities in your Office 365 environment, ensuring robust protection against cyber threats and compliance with industry standards.
Google Cloud
Our Google Cloud Security services help you proactively identify and remediate vulnerabilities in your Google Cloud Platform (GCP) environment, ensuring robust protection against cyber threats and compliance with industry standards.