Purple Teaming
Our Purple Teaming services help you proactively identify and remediate vulnerabilities by combining the strengths of both Red Team and Blue Team approaches, ensuring a holistic and robust defense against cyber threats.
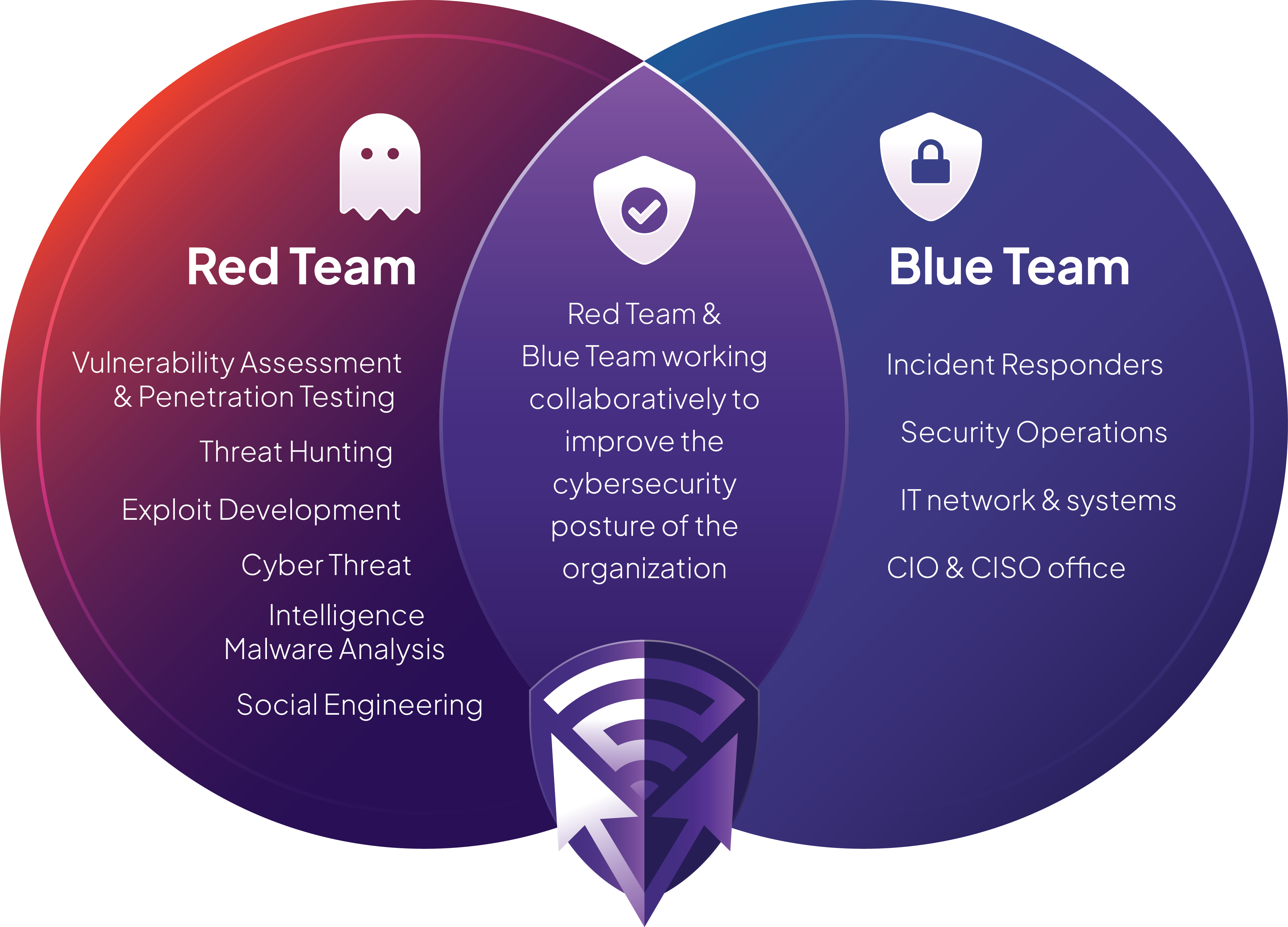
The Importance of Purple Teaming
In the ever-evolving landscape of cybersecurity, it is crucial to adopt a collaborative approach to defense. Purple Teaming integrates the offensive strategies of Red Teams, who simulate attacks, with the defensive tactics of Blue Teams, who protect against these threats. This synergy enhances the ability to identify, understand, and mitigate vulnerabilities effectively, ultimately strengthening your organization’s security posture.
Our Approach
At Pretera, our approach to purple teaming is collaborative and dynamic, emphasizing the integration of offensive and defensive strategies. We begin by preparing the environment for collaboration, ensuring clear communication between red (offensive) and blue (defensive) teams. This involves sharing intelligence and identifying key objectives to enhance our collective understanding of threats.
Next, we conduct joint exercises where the red team simulates real-world attacks, while the blue team actively defends against these scenarios. This hands-on engagement allows us to assess and refine defensive capabilities in real time. Over the course of these exercises, we analyze the effectiveness of existing security measures, identify gaps in defenses, and adapt our tactics accordingly.
Finally, we focus on knowledge sharing and continuous improvement, capturing insights and lessons learned to strengthen our security posture. By fostering a culture of collaboration and learning, our purple teaming approach enhances resilience against evolving threats and promotes a proactive security environment.
Key Features of Our Purple Teaming Services
- Collaborative Exercises: Facilitating joint exercises between Red and Blue Teams to enhance threat detection and response capabilities.
- Attack Simulations: Conducting realistic attack simulations to test and improve defensive strategies.
- Response Drills: Evaluating and refining incident response protocols through practical exercises.
- Threat Hunting: Integrating Red Team tactics into Blue Team operations to proactively seek out and address hidden threats.
- Active Defense: Utilizing advanced threat hunting techniques to identify and mitigate potential vulnerabilities.
- Continuous Improvement: Applying insights gained from threat hunting to enhance defensive measures.
- Knowledge Sharing: Encouraging open communication and knowledge transfer between Red and Blue Teams to build a more resilient security posture.
- Workshops and Training: Conducting workshops and training sessions to share best practices and lessons learned.
- Regular Debriefs: Holding regular debrief sessions to discuss findings and areas for improvement.
- Customized Scenarios: Developing tailored attack and defense scenarios to address specific risks and challenges faced by your organization.
- Industry-Specific Threats: Focusing on threats relevant to your industry to provide targeted protection.
- Adaptive Strategies: Continuously updating scenarios to reflect the latest threat intelligence.
- Comprehensive Reporting: Providing detailed reports that outline identified vulnerabilities, the effectiveness of defenses, and recommendations for improvement.
- Executive Summary: High-level overview for stakeholders.
- Technical Details: In-depth analysis for your IT and security teams.
- Remediation Guidance: Step-by-step instructions to fix identified issues.
Detailed Reporting and Remediation Guidance
Our detailed penetration testing report is written in understandable terms and provides clear and actionable information about identified vulnerabilities, their potential impact, and recommended remediation steps. This allows your team to quickly understand and start addressing issues immediately.
- Executive Summary: High-level overview of the findings aimed for management and delivered shortly after the assessment.
- Technical Details: In-depth reporting with details at every step of our penetration testing services, helping your technical teams replicate the vectors easily and remediate swiftly.
- Report Readout: We provide report read out for your management, accelerating the understanding of the report and clarifying any unclarities on the spot.
- Remediation Guidance: Post-pentest step-by-step support and guidance on how to fix identified vulnerabilities and accelerate the remediation
- Free Retesting: Following the remediation of identified vulnerabilities, we offer a free retesting of all the vulnerabilities to ensure everything has been remediated.
Why Work With Us
Our team of experienced security professionals brings deep knowledge and experience of application security and the latest threat landscapes. We operate as your internal team, seeking to always understand the challenges you face and ensure you solve them, always. Work with us and experience open and transparent communication throughout the testing process providing real-time updates and insights. This collaborative approach ensures that you are always informed and can prioritize remediation efforts.
KeyPoints
-
Offensive and Defensive Collaboration
-
Threat Response Optimization
-
Proactive Security Posture
-
Evolving Threat Adaptation
-
Integrative Cybersecurity
-
Sophisticated Attack Simulations
Related Certifications
-
Offensive Security Certified Expert
-
Offensive Security Web Expert
-
AWS Certified Cloud Practitioner
-
Certified Ethical Hacker
Our Approach
-
We Assess
After an initial call with the client, Pretera will start working on scoping and based on the required amount of the time required to complete the work, the client will receive a detailed offer.
-
We Prevent
During the assessment phase, Pretera will provide its services for which the client has paid for, and it could range from a few days assessment to a several weeks assessment.
-
We Secure
Upon completion of the assessment, Pretera will deliver a detailed report of findings to the client and will offer a walk-through presentation if asked by the client.



